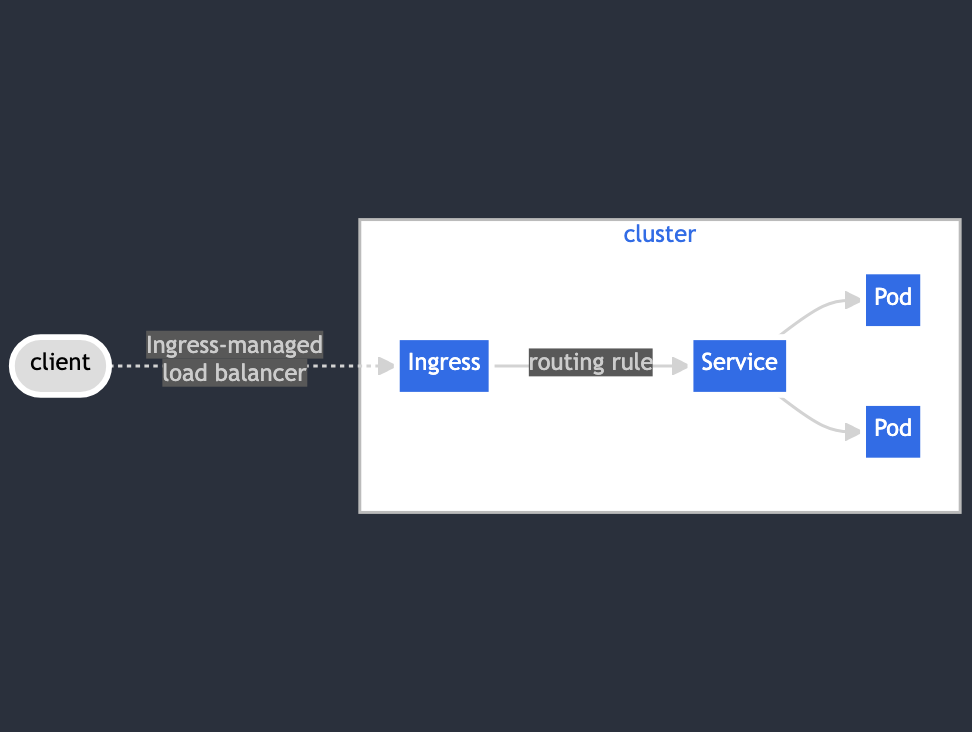
A Container Network Interface (CNI) plugin implements the underlying software-defined network infrastructure. Every cluster has some plug-in that manages the CNI implementation. The CNI handles IP assignment, routing, and policy enforcement for the Pods, Services, and Network Policies.
This section explores CNIs that can expand on the Kubernetes baseline features. Picking the right CNI for you is important because not all CNI plug-ins implement the same features. For example, some CNIs do not implement Network Policies.
Flannel
Flannel is a simple-to-deploy CNI that focuses on the communication between pods. It is popular and can be integrated with other solutions to make a complete offering. It is relatively low on resource consumption and will not incur extra costs. It is a good CNI option if you want to implement an external firewall.
Calico
Calico is a popular CNI for Kubernetes with many features and benefits. It is lightweight and resource-efficient. It runs as a distributed workload, so its components run on each node. Calico offers both Kubernetes networking features and Network Policies. It supports advanced features like policy ordering/priority and has flexibility in its match rules. It also has built-in logging, monitoring, and auditing tools. The open-source version of Calico is free and offers enterprise support. The only downside is that Calico is moderately complex with a steep learning curve.
If your environment has VMs and bare-metal devices, you can use Calico to firewall all those endpoints as well.
OVN-Kubernetes
If you use Red Hat’s OpenShift, OVN-Kubernetes is the default CNI. It can provide networking, Network Policies, and load-balancing capabilities. It is meant to be run on a large scale and moderately consumes resources. It has a distributed architecture, meaning that components run on each node and keep the overall resource usage low per node. It is open-source and free to run as well.
However, it is built on top of the Open Virtual Network (OVN), so there can be a learning curve working with both.
OVN-Kubernetes can integrate with external load balancers and gateways and is a good choice if the cluster is part of a larger hybrid environment. Overall, it may be a good option if you are running a medium—to large-scale cluster and are already familiar with networking and OVN.
Cilium
Cilium is one of the more advanced CNIs, providing networking, Network Policies, load balancing, and service mesh integration and observability. It leverages eBPF (extended Berkeley Packet Filter) technology to operate at the kernel level. eBPF allows Cilium to operate with higher efficiency and performance while maintaining moderate resource usage. However, it is relatively complex and has a steep learning curve.
Much like Calico, Cilium is open source and free to run, and there is commercial support.
Another area in which Cilium shines is in its observability and monitoring features. Its built-in platform, Hubble, provides visibility into network traffic and keeps detailed metrics, logs, and network traces.