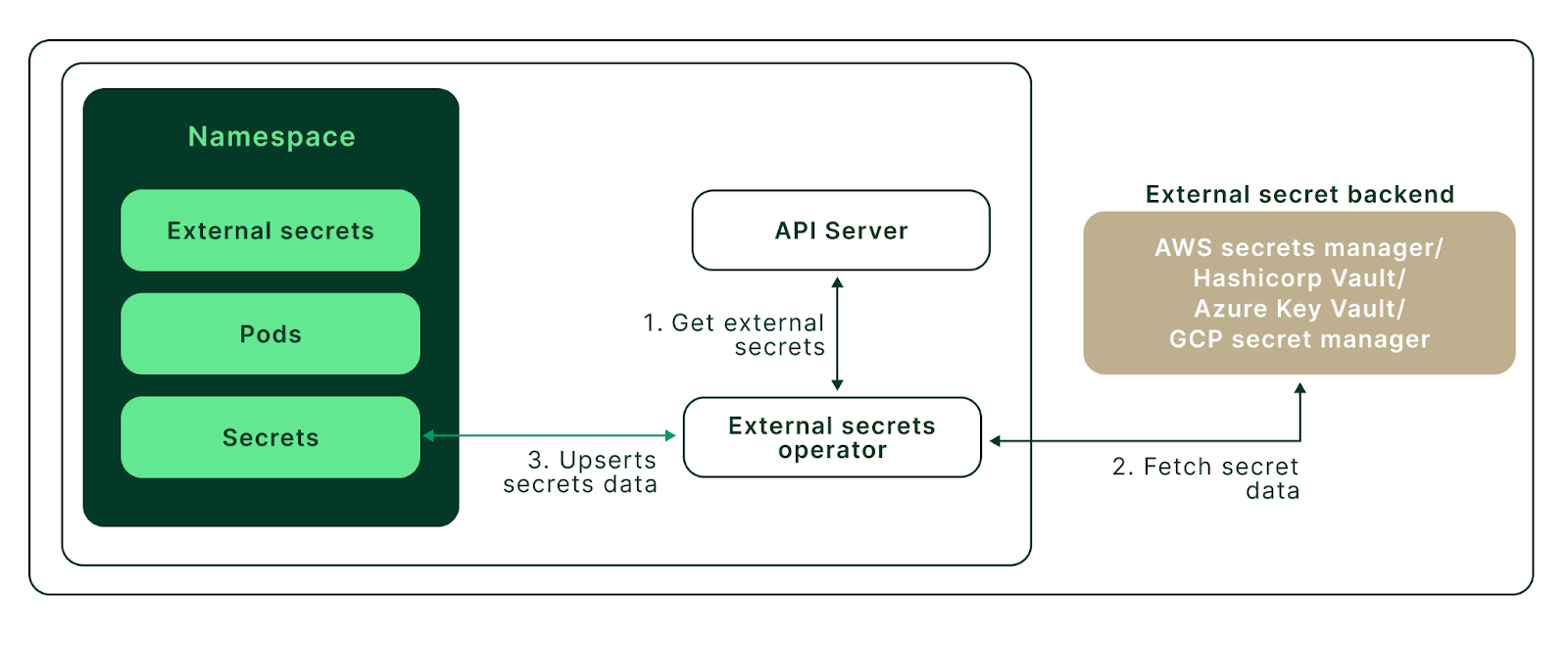
Secrets with AWS Secrets Manager
To demonstrate Kubernetes External Secrets, we will use Amazon Elastic Kubernetes Service (EKS) as a Kubernetes Cluster and Amazon Secrets Manager as an external secret store.
To follow this tutorial, you’ll need:
Deploying AWS EKS Cluster
To deploy an AWS EKS cluster, we will use eksctl CLI. To create the cluster, create a cluster.yaml manifest file with the below configuration.
apiVersion: eksctl.io/v1alpha5
kind: ClusterConfig
metadata:
name: eks-external-secrets
region: us-east-1
nodeGroups:
- name: ng-1
instanceType: t3.small
desiredCapacity: 1
volumeSize: 8
To apply the configuration, run this command in your terminal:
$ eksctl create cluster -f cluster.yaml
This will create an EKS cluster with one node group containing a single node in the us-east-1 AWS region. Once the cluster is ready, you should see output similar to the output below.
2022-09-05 18:47:47 [✔] EKS cluster "eks-external-secrets" in "us-east-1" region is ready.
Now, we can use this cluster and interact with it using kubectl. First, we must update the kubeconfig file with newly created cluster access. To update the kubeconfig, execute the below command.
$ aws eks --region us-east-1 update-kubeconfig --name eks-external-secrets
Test cluster access by running:
$ kubectl get pods
No resources found in default namespace.
Deploying External Secrets Operator
Install Helm to deploy the External Secrets Operator in the cluster. Once installed, verify the Helm version.
$ helm version --short
Next, install the External Secrets Operator from the Helm chart repository external-secrets by executing the below commands:
$ helm repo add external-secrets https://charts.external-secrets.io
$ helm install external-secrets \
external-secrets/external-secrets \
--namespace external-secrets \
--create-namespace \
--set installCRDs=true
Once installation is complete, you will see the below message:
external-secrets has been deployed successfully!
Configuring IAM roles for service accounts (IRSA) and Secrets Manager
With IAM roles for IRSA, you can map AWS IAM roles to Kubernetes Service Accounts. This feature allows you to manage AWS credentials for your applications running on EKS without managing static credentials directly.
To securely use External Secrets, we will use IRSA to provide AWS credentials. This way, the External Secrets pods will have access only to the secrets they need in our AWS Secrets Manager secret.
To use IRSA, the first step is to create an IAM OIDC Provider for your cluster (if one doesn't already exist). After you associate the provider with your EKS cluster, you can create an IRSA service account that External Secrets will use.
To enable IAM OIDC Provider for your cluster, run the following command:
$ eksctl utils associate-iam-oidc-provider --cluster=eks-external-secrets --approve
Now, we will create a secret in AWS Secrets Manager. Create a secret with the name secret-api-key and store the username and key as secret values.
$ SECRET_ARN=$(aws secretsmanager create-secret --name secret-api-key \
--secret-string "{\"username\":\"admin\",\"key\":\"SeCure@ApIKey\"}" \
--region us-east-1 | jq -r .ARN)
Next, create an IAM policy that will grant the permissions to interact with AWS Secrets Manager. For additional security, the following policy only allows for the description and retrieval of a single specified secret.
$ IAM_POLICY_ARN=$(aws iam create-policy --policy-name eks-external-secrets-reader --policy-document '{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"secretsmanager:DescribeSecret",
"secretsmanager:GetSecretValue"
],
"Resource": ["'${SECRET_ARN}'"]
}
]
}' | jq -r .Policy.Arn)
Finally, create an IRSA service account for the External Secrets Operator to authenticate and fetch the required secrets from AWS Secrets Manager.
Here we are creating this IRSA service account in the default namespace.
$ eksctl create iamserviceaccount \
--name external-secrets-irsa \
--namespace default \
--cluster eks-external-secrets \
--role-name "external-secrets-irsa-role" \
--attach-policy-arn $IAM_POLICY_ARN \
--approve \
--override-existing-serviceaccounts
To verify the successful creation of the Kubernetes Service Account, execute the following command:
$ kubectl get sa
NAME SECRETS AGE
default 1 39m
external-secrets-irsa 1 3s